Q5 Safe & Secure: Leveled Security
MOBILE SAFETY AND SECURITY INTRODUCTION
Mobile phones are everywhere. They are just as important as safety and security when using a digital computing device; in fact, they are one of the more powerful options used today by many.
Step 1. Read the infographic on Cell Phone Safety.
Step 2. Discuss it with a partner or as a class based on your teacher's instructions.
- What three points from this infographic stand out to you as most important?
- Do your points align with your partners? You should each discuss why you believe your three points are the most important.
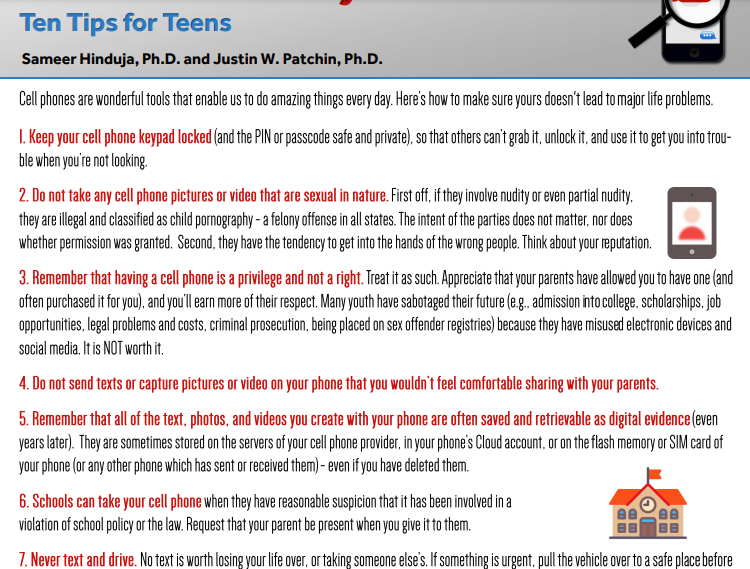
© 2018 Cyberbullying Research Center | cyberbullying.org Reproduction allowed for non-profit educational purposes only.
Two-Factor Authentication (2FA)
2FA sounds fancy, but it’s really just an extra lock on your online accounts. Think of it like this: instead of just needing your password (one key), you also need a second key—like a code texted to your phone. So even if someone steals your password, they still can’t get in without that second step. 2FA is like having a secret handshake for your account that only YOU know!
As you play the video below, think about where you have had to use 2FA or where you think it should be used.
Trend Micro Cyber Academy - Two Factor Authentication
Direct link (2:34 min.)
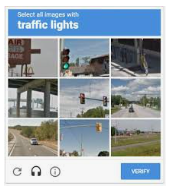
Sometimes 2FA makes you solve a quick puzzle before logging in—like clicking on all the pictures with traffic lights, crosswalks, or even animals.
- Have you ever had to do this before signing in?
Competencies & Standards
MITECS Michigan Integrated Technology Competencies for Students, and
3. Knowledge Constructor
a. Plan and employ effective research strategies to locate information and other resources for their intellectual or creative pursuits
Websites and Documents
Websites
Videos from Outside Sources




